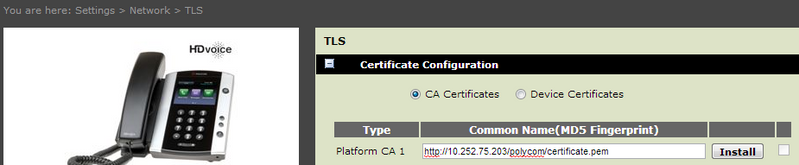
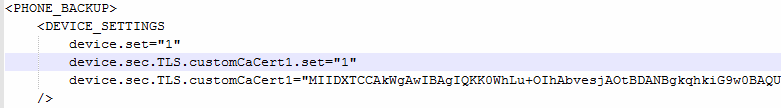
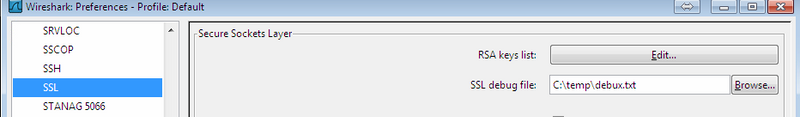
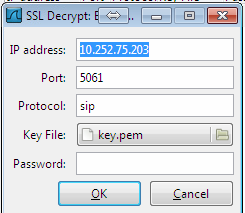
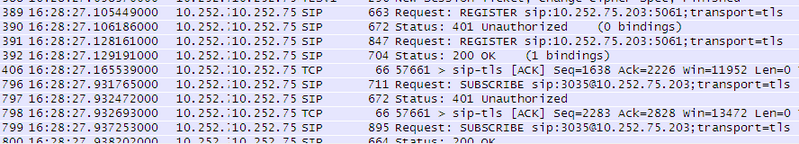
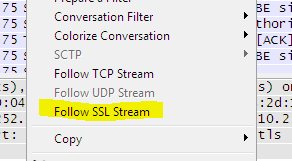
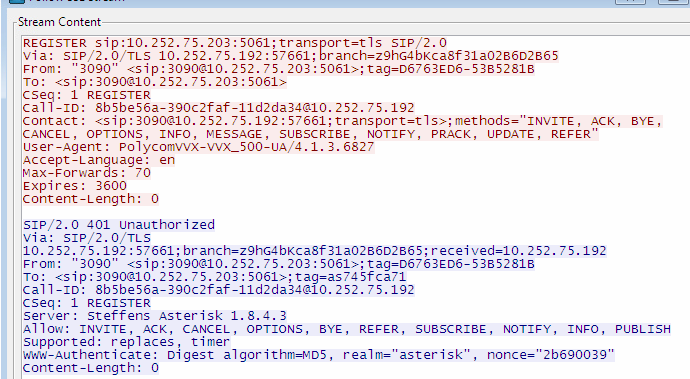
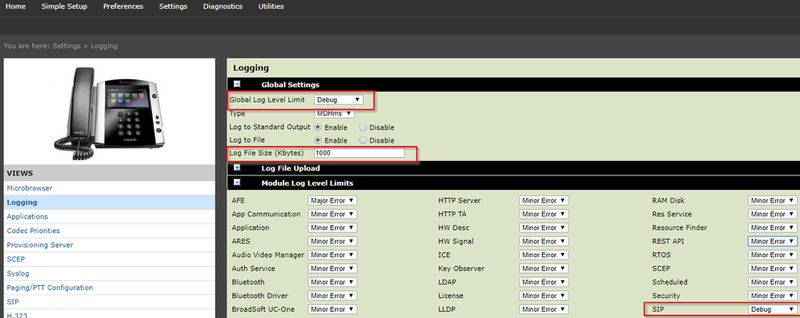
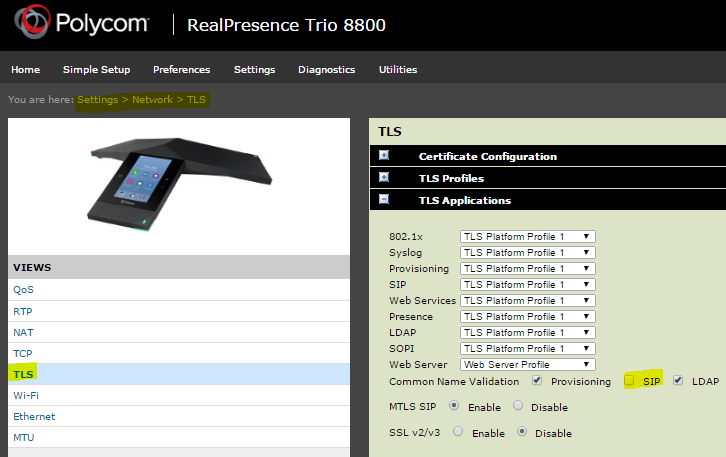
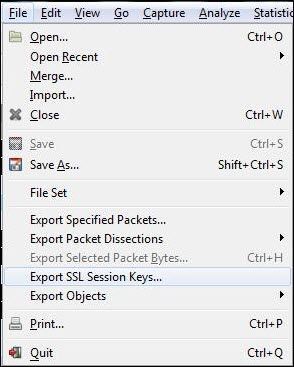
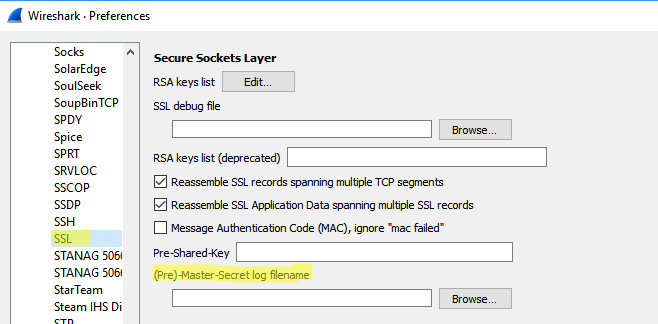
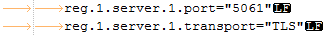[FAQ] How can I setup a TLS connection for SIP signaling and / or troubleshoot this?
Options
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
turn on suggested results
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Guidelines
The HP Community is where owners of HP products, like you, volunteer to help each other find solutions.